Before we discuss Shut Up and Dance, let’s take a look back to when this episode was first released: October 21, 2016.
In 2016, commercial drones experienced a significant surge in popularity, with companies like DJI dominating the market. According to Gartner, the industry for commercial drones was valued at $2.8 billion.
Beyond their application as flying cameras, commercial drones brought to light various privacy concerns and raised questions about the delicate balance between safety, surveillance, and the protection of human rights.
Apart from law enforcement and government agencies, tech companies were also closely monitoring us. In 2016, Google made a change to its privacy agreement, allowing it to link users’ search history with personal information, including their names. Consequently, advertisers gained the ability to target individuals directly by their names. When questioned, a Google spokesperson explained that it was aligned with the way people use smartphones and how ads are viewed across multiple devices.
In late 2015, following the tragic San Bernardino shooting where 14 people lost their lives, the FBI obtained an iPhone but was unable to access the data due to the encrypted lock screen. Confronted with an unprecedented dilemma, Apple made a significant decision: it chose not to yield to the government’s demand to create a backdoor, primarily because of the potential security risks it could pose in the future.
During this time, it seems like everyone wants a piece of our information rather to sell us stuff, protect us, or scam us. 224,000 ransomware attacks in Australia were detected between April and May 2016 alone. These types of attacks require little technical skills and allow hackers to access the victims’ computers, much like how Shut Up and Dance’s protagonist, Kenny’s computer was hacked.
2016 was a year before Playboy founder, Hugh Hefner’s death and the rise of the Me Too movement. Society was still grappling with the issue of protecting misogynistic individuals and their right to perpetuate toxic behavior.
This was starkly evident in the infamous 2005 hot mic incident involving Donald Trump during an Access Hollywood segment with Billy Bush. In that incident, Trump openly professed that he could do whatever he wanted with women, even going as far as making inappropriate comments about “grabbing them.” Despite this scandalous revelation, Trump’s actions did not prevent him from ultimately becoming the 45th President of the United States.
However, there was a shift in societal attitudes, both in the digital and physical realms.
In 2016, the world began to redefine its understanding of what is considered right and wrong. An example of this change was seen with the South Korean website Sora.net, which published spy-cam porn. After some victims depicted in the videos tragically took their own lives, there was a significant campaign against the website, resulting in its official ban.
During the trial of Brock Turner, a Stanford student convicted of sexually assaulting a woman, his father stepped forward to defend him. He minimized his son’s actions, referring to the charges as a “steep price to pay for 20 minutes of action…” and attempted to portray his son as depressed. The public was appalled by this defense and united to make it clear that Turner and his father could not be seen as victims in this situation.
In April 2016, a California woman filed a lawsuit against Jeffery Epstein and Donald Trump, alleging that the two billionaires assaulted her at a series of parties in 1994 when she was just 13 years old. Notably, it would take three more years before Epstein was finally arrested for his involvement in trafficking minors.
Let’s not forget about Jared Fogle, the disgraced Subway spokesperson. We all know what he did. He was arrested in July 2015.
Indeed, the mid-2010s was a troubling period marked by various forms of exploitation and ambiguity. The legal system, in an effort to catch a new breed of criminals, seemed to be navigating uncertain territory, blurring the lines of ethics. Naturally, those who had made a habit of crossing the line were finally getting caught. And that is what brings us to this episode of Black Mirror, episode 3 of season 3: Shut Up and Dance.
In this video, I will explore three key themes from the episode and analyze whether similar events or concepts have occurred in recent years. Furthermore, I will assess whether these scenarios remain plausible in the present day.
Take a deep breath. This one is going to be a doozy.
Deviant People and Infected Machines
The story centers around Kenny, a regular teenager who works at a restaurant and comes across as a kind individual. However, things take a turn when his sister borrows his computer to download videos, inadvertently installing malware. This event reveals that there’s more to Kenny than his affable exterior suggests.
Malware, or malicious software, has evolved alongside computers since the 1970s. The initial case was “The Creeper,” an experimental program that infected the TENEX operating system, showing the message “I’m the creeper, catch me if you can!” Though not directly harmful, it could replicate and spread. In response, the first antivirus program, “The Reaper,” was created to eliminate and halt its wider dissemination.
Over time, malware has grown in complexity and variety due to computer networks, the internet, and modern operating systems. According to a report by Symantec Corp., from 2016 to 2017, malware variants doubled with 669,947,865 different variants. Today, it includes viruses, worms, Trojans, ransomware, spyware, and more.
Spotting computer viruses, like uncovering frauds and scams, remains a perpetual cat-and-mouse pursuit. Just as one deceptive approach is terminated, a fresh one arises.
Tech Support Scams are a prime example. Here, impostors pretend to be tech support from respected firms via unexpected calls or deceptive computer ads. They allege device problems, coaxing victims into granting remote access or paying for needless services.
GPS trackers have become a widespread tool. In 2021, Apple introduced the Airtag, initially designed as a key or luggage finder that owners can track if they lose or become separated from their belongings. However, there have been several incidents of Airtags being planted on individuals and misused as stalking devices.
In today’s world, there is a constant fear of harmful individuals gaining access to our sensitive data. Victims find themselves compelled to comply with the scammers’ demands to prevent their private information from being exposed. Typically, scammers engage in such illegal activities for financial gain.
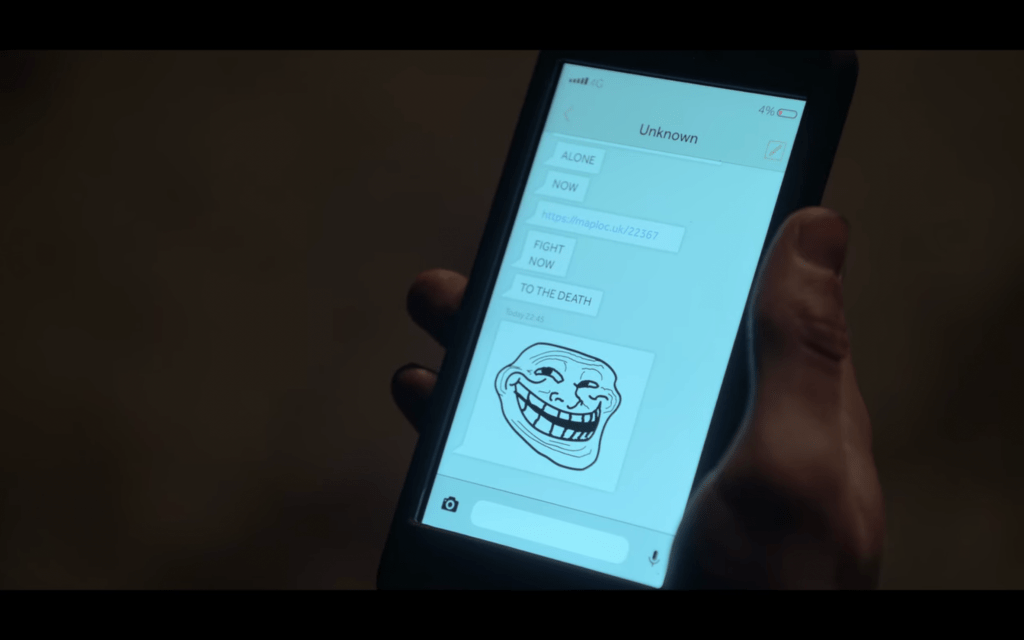
However, in the story of Shut Up and Dance, we witness a unique twist where the victims are unwittingly drawn into a wild goose chase, only to discover later that the virus and scams were orchestrated as a form of retribution, revealing that the victims themselves had engaged in wrongful doings.
We are quick to judge people, particularly their online behavior. Criticizing others on the internet has become commonplace, and with the emergence of cancel culture and doxing, nobody is immune to having their privacy exposed to the world. Unfortunately, the impact on the individual is often overlooked.
In 2015, a tragic incident occurred when 13-year-old Izabel Laxamana committed suicide after her father—as punishment— publically shamed her by cutting off her hair on video and sharing it on YouTube. Evidence of private events left in reckless hands becomes a potent weapon. A father using social media to punish his daughter had more force than he knew. Nearly a decade later, we are only starting to recognize the cost of public shaming and more importantly the difference between discipline and punishment.
In the case of the vigilante hacker in Shut Up and Dance, their act of indifference towards Kenny and the other victims, sending the Troll face instead of prioritizing their pursuit of justice, raises doubts about their genuine moral integrity.
There is a valuable lesson to be learned from this episode. If you ever find yourself in a situation where someone is threatening to expose private data about you, remember one crucial rule when dealing with blackmail: Do Not Comply with the Blackmailer’s Demands, whether it involves paying a ransom or fulfilling their requests. Complying with their demands does not guarantee that they will keep their word, and it can even encourage more blackmail attempts, as demonstrated in this episode.

Privacy: Curtains or Locks
In this episode, a recurring theme is privacy and how technology dismantles the barriers that protect us during our most vulnerable moments, exposing us to the world.
When we talk about privacy, it’s not about whether we have secrets or not. We all have things we want to keep to ourselves. Privacy gives us the freedom to make our own choices without worrying that the government or criminals will use our personal information against us.
Although hackers can’t physically harm us, they can inflict indirect damage. They can coerce us into increasingly perilous situations, ensnaring us further within a criminal network.
In 2017, the Equifax data breach compromised the personal details of about 147 million people. A substantial portion of this data such as names, Social Security numbers, birth dates, addresses, and credit card data was suspected to have been sold on black markets.
Back in 2016, there was a picture of Facebook’s CEO, Mark Zuckerberg, using a laptop with tape covering the camera. For many, this confirmed that hackers could turn on your computer’s camera without you knowing.
Various types of malware can seize control of a laptop camera. A prime example is a Remote Access Trojan (RAT), a harmful program that hands attackers remote control over a victim’s computer.
While CEOs and public figures worry about privacy breaches due to their involvement with sensitive information, women are especially vulnerable to these attacks.
In November 2013, 20-year-old, Jared James Abrahams pleaded guilty to hacking over 100 women’s computers and installing the highly invasive malware Blackshades in order to obtain sensitive images and videos of them. He got 18 months for that crime.
In the pandemic’s early months, as education went virtual, unauthorized people began intruding into online classes via Zoom, causing disruptions. These disruptions included sharing inappropriate content, making noise, and harassment. Sacrificing convenience for security, Zoom and educational institutions took measures to bolster defenses against Zoom bombing.
Government agencies like the FBI’s core mission involve enforcing federal laws and tackling cybercrime and online dangers like hacking, identity theft, fraud, terrorism, and child exploitation.
An instance of the FBI apprehending online sexual predators via surveillance is the 2015 case of Operation Pacifier, also referred to as the Playpen case. As a result of Operation Pacifier, the FBI was able to identify and arrest hundreds of individuals worldwide. While the operation was a success, the approach left many wary. It sparked debates about the ethical implications of law enforcement engaging in hacking activities and the potential challenges to privacy rights.
Surveillance is available to the “good guys” and the “bad guys.” It not only reveals criminals but our most private moments, feelings, and thoughts, making it difficult to trust anyone or anything around us.
It only takes one dumb decision caught on camera to destroy our reputation. “Shut Up and Dance” illustrates the paramount importance of privacy for that reason. Anyone could be caught with their pants down. So today, we are left with a question: how do we find the right balance between cautious sanity and controlled paranoia?

Pornography and Everything that Comes After
The show doesn’t explicitly state what Kenny was watching, but it’s clear it involved minors, as his mother strongly condemns it at the end of the episode.
Thanks to the Internet, pornography—like communication and knowledge—is now more accessible and diverse than ever. This has enabled a broader and deeper exploration of fetishes, giving rise to communities like Looners (balloon fetishists), ABDL (Adult Baby/Diaper Lover role-playing), and Furries.
The impact of pornography on sexual attitudes and behaviors is an ongoing debate. Research indicates that exposure to certain types of pornography might lead to more permissive views about casual sex, unrealistic expectations, and acceptance of aggressive or non-consensual behavior. Some even link excessive pornography to millennials having less sex than earlier generations.
With that being said, views about the adult industry are also shifting due to the internet. Individuals are now empowered to create and share explicit content via social platforms, webcams, and amateur sites, blurring the line between consumers and creators.
Popular subscription platform, OnlyFans helped usher a new phase of adult content and sex work by promoting personal freedom and destigmatizing the industry. As it became acceptable to engage with pornography without shaming, the focus shifted to consumer protection. Much like the YouTube adpocalypse, a similar trend played out within the gated walls of OnlyFans.
In August 2020, actress and model Bella Thorne initially promised to share exclusive explicit content on her OnlyFans account. Yet, when her content was eventually released, the many misled subscribers were outraged to find that her content didn’t align with the implied explicitness.
The situation got more intense when news came out that she made over a million dollars on her first day of releasing content. This whole thing highlighted the problems that arise when famous people join platforms like OnlyFans. As a result, changes in OnlyFans’ rules ended up affecting how much money many creators made.
Today, we’re more accepting of the fact that producing adult content is a decision made personally, with considerations of informed consent, boundaries, and individual circumstances.
On the flip side, unsolicited explicit images, known as “dick pics,” is still considered a disrespectful act, often a form of harassment. This digital form of flashing surged with the advent of camera phones. According to a 2017 YouGov survey, 46% of women had received unsolicited dick pics, with 22% of men admitting to sending them without consent.
A memorable example was in 2010 when former football player Brett Favre was accused of sending “dick pics” to a female New York Jets employee. The incident garnered media focus and led to NFL fines.
While dick pics are generally unwelcomed, a large portion of men who send them (44%) are expecting a similar picture in return. An act of naivety rather than malice. But alas, the realm of online pornography can get much darker.
The now-defunct IsAnyoneUp.com was infamous for being a hub for sexually explicit content distributed without the subject’s consent, also known as revenge porn. This resulted in legal actions against the creator and so-called “professional life ruiner”, Hunter Moore.
And still, the Internet got even darker—
In 2017, a video surfaced where British commentator, Milo Yiannopoulos seemed to defend pedophilia. His controversial comments caused him to step down from Breitbart News. The downfall of Yiannopoulos, already a contentious right-wing figure, demonstrated that some topics have no room for debate.
YouTube always had strong rules against sexual content and pornography, but up until 2019, YouTube did little to protect children and younger users. The video-streaming company was often criticized for allowing inappropriate content targeting children to evade its moderation systems. What really opened their eyes was the serious legal issues they faced. By collecting information from users under the age of 13 without parental consent, they violated the Children’s Online Privacy Protection Act (COPPA), which cost them $170 million.
Today, YouTube is making a commitment to safeguarding children and young users. One key approach was introducing a policy that limits or prevents comments on videos featuring minors.
As we strive to stay safe, we should also be wary of conspiracy theories online, most notably those linked to extreme right-wing groups. These false claims often suggest large pedophile rings or powerful figures involved in such activities. These stories are designed to destroy the reputation of opponents and spread distrust in institutions.
Take the 2016 Pizzagate conspiracy, for instance. It wrongly alleged a D.C. pizzeria was a hub for child sex trafficking involving high-ranking Democratic officials, including Hillary Clinton. Despite being debunked, it gained attention and led to a shooting at the pizzeria.
If you grew up in the 2000s like me, you might remember the show “To Catch a Predator,” hosted by Chris Hansen. The reality television series aimed to expose individuals arranging sexual encounters with minors through online chats. The show collaborated with law enforcement for sting operations, leading to arrests at meet-up locations. Although the exact number is unclear, it is estimated that dozens were apprehended. In the new age of the internet, To Catch a Predator prompted discussions about online safety, despite facing ethical criticisms and questions about entrapment.
And that is where Shut Up and Dance sits. Like Chris Hansen, Kenny’s hackers operated in a grey area, albeit the shades are different. In fact, much of the Internet resides there now—neither purely good nor evil. We all breathe and sweat on this spectrum of allure and anxiety, which is what makes this episode so impactful. In the digital world, nobody is safe, we are all susceptible to scams, exposure, and reputational damage.
“Shut Up and Dance” warns against getting too comfy online. Just like computers, we need to scan to detect viruses within, whatever might be messing up our “operating system.” What can be this anti-virus for our human soul? Certainly, that’s not something we can find on the Internet. Or can we?
Join my YouTube community for insights on writing, the creative process, and the endurance needed to tackle big projects. Subscribe Now!
For more writing ideas and original stories, please sign up for my mailing list. You won’t receive emails from me often, but when you do, they’ll only include my proudest works.